
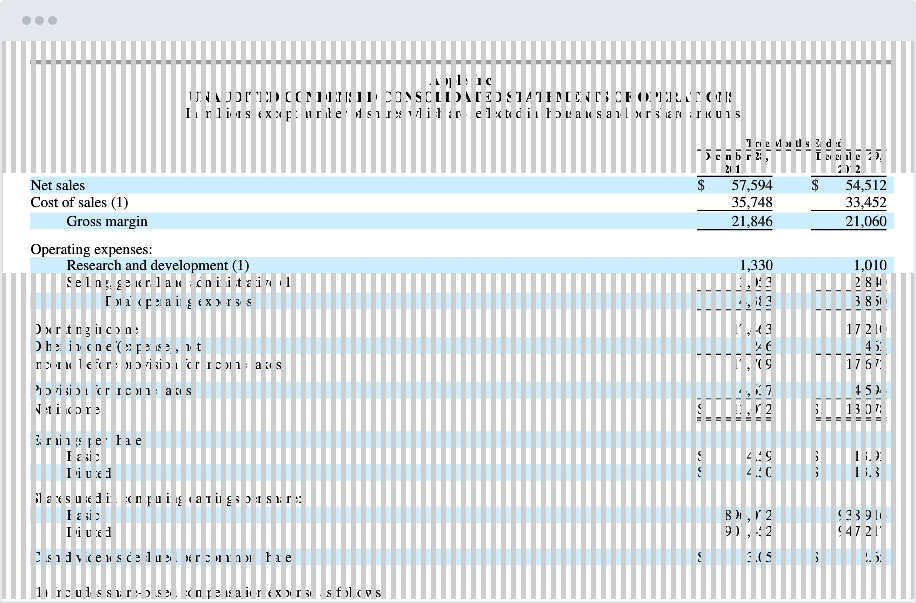
When choosing a virtual data room (VDR), perhaps the main concern on most people’s minds is data safety. For that, robust security features are paramount — a secure VDR ensures your confidential information stays safe during sharing, storage, and all kinds of collaboration.
With the right safeguards, you’ll be protected against unauthorized access, data breaches, and regulatory non-compliance, maintaining your information in trusted hands at all times. Without them, you could join the 47% of US firms that suffered severe financial loss through data breaches and similar attacks.
Why virtual data room security matters
Research shows that businesses are increasingly relying on VDRs for mergers, acquisitions, financial audits, legal cases, and other corporate processes. Why?
These and other use cases have one thing in common: the need for confidentiality. After all, we are talking about environments where the risk of data breaches, leaks, or unauthorized access could result in significant financial losses, reputational damage, or legal penalties.
This is where virtual data rooms step in. The best VDR for security will provide you with a secure platform for file sharing coupled with the best that tech has to offer in the way of security and collaboration features.
Increasing regulation
Another primary reason why VDR security is so important is the role it plays in ensuring compliance with industry standards and regulations. Think the finance, healthcare, and legal industries — all with strict data protection requirements.
Here, too, a good VDR makes all the difference. Virtual data rooms with robust security features help businesses meet compliance standards, such as ISO 27001, SOC 2, and FINRA regulations. Without them, companies may be left to face non-compliance issues, with the looming shadow of hefty fines or unwanted legal repercussions.
Bottom line: It’s crucial to choose the right VDR provider, one that puts a premium on the security aspect of the job, ensuring compliance with certification standards and making sure to protect sensitive data at all times.
Popular secure data rooms
Overall rating:
4.9/5
Excellent

Overall rating:
4.8/5
Excellent

Overall rating:
4.7/5
Excellent
Key security features of a virtual data room
Virtual data rooms are essential for protecting sensitive data, but there are a few features that are essential to any data room worthy of the name. Below are some of the key security features that ensure your information remains safe and compliant.
Encryption and data protection
Encryption is everywhere in our modern, digital world. But not all encryption standards are the same. So how much of it is up to the task of securing company secrets and sensitive data?
AES 256-bit encryption is widely accepted as the most robust commercially available form of encryption, and is a critical security measure in VDRs, ensuring that files remain unreadable to unauthorized users.
A good VDR will encrypt data to protect sensitive information both in transit and at rest, preventing data breaches and ensuring compliance with data protection regulations. Strong encryption is especially important for secure file sharing, safeguarding documents during transfers and access from third parties.
Multi-factor authentication
Multi-factor authentication (MFA) adds an extra layer of security by requiring users to verify their identity when logging in from new devices or locations. This helps protect against unauthorized access, even when user passwords are compromised. While rarely seen in the early days of the internet, multi- or two-factor authentication is now the gold standard, and you should not consider using a data room that does not provide it.
Access control
Access control features (also known as granular access) are what allows administrators to set specific permissions, ensuring only authorized users can access or modify sensitive files.
Permissions can be set to view-only, comment, edit, and download, among others.
When sharing content with another company for due diligence, for instance, it can be essential to restrict access to certain files that only key stakeholders should be able to view. This is one of the many situations where proper access control is a fundamental tool for ensuring you can share, but protect your info.
Audit trails and activity monitoring
Audit trails provide transparency by allowing admins to track user actions within the VDR — including details such as access time and date, which files were viewed and for how long, files downloaded or edited, what locations your files were accessed from, and so on.
The audit trail feature is a sine qua non in activity monitoring, allowing administrators to keep an eye on document accesses and identify any suspicious activity, with obvious rewards for the security and compliance levels of your organization.
On top of this user action history, user activity tracking in VDRs can sometimes be viewed in the shape of comprehensive logs, often available in easy visual report format. This helps businesses meet regulatory requirements and maintain accountability, and is another key feature in what to look for in a VDR.
Compliance and certifications to look for
When selecting a virtual data room, you want to make sure it meets key industry certifications and compliance standards, thereby safeguarding sensitive data and avoiding legal risks. Typically, the below certifications will as good as guarantee that the VDR adheres to stringent security practices and data protection regulations.
ISO 27081
ISO 27081 is the top security standard for cybersecurity and privacy in cloud storage and VDRs, focused on protecting personally identifiable information (PII) in cloud environments. A VDR with ISO certification ensures robust data protection measures, including encryption, access control, and privacy management.
SOC 2
SOC 2 (Service Organization Control 2) compliance ensures that a VDR meets high standards for data security, availability, confidentiality, and privacy. SOC compliance is especially important for businesses handling sensitive customer data, ensuring the VDR follows best practices for safeguarding information and maintaining operational integrity.
FINRA compliance
For companies in the finance and legal spheres, FINRA (Financial Industry Regulatory Authority) compliance is a must. VDRs that comply with FINRA regulations meet strict standards for data protection and reporting, ensuring that financial documents are handled securely and in line with industry-specific guidelines.
GDPR
GDPR (General Data Protection Regulation) compliance ensures that a VDR adheres to strict standards for handling personal data from the European Union. This compliance is vital for businesses that process sensitive information, as it mandates explicit consent for data usage, the right to be forgotten, and data portability.
A GDPR-compliant data room implements robust security measures, such as encryption and access controls, while maintaining transparency through detailed audit trails.
HIPAA
A HIPAA-compliant data room deploys all the requisite tools to safeguard sensitive patient information through security standards such as encryption and access controls — crucial for healthcare organizations looking to securely share electronic protected health information (ePHI) while maintaining audit trails for compliance. HIPAA-compliant VDRs help protect patient privacy and avoid regulatory penalties.
These and other certifications provide peace of mind, confirming that the data room has been thoroughly vetted and that it meets the necessary security and regulatory standards.
How to choose the right VDR for your business
Selecting the right virtual data room involves evaluating various factors to ensure it aligns with your security and operational needs. Let’s take a look at some key steps to guide your decision-making process.
1. Assess security features
When choosing a VDR, prioritize its security features. These can include:
- 256-bit encryption. All top level data rooms will feature bank-grade data encryption methods.
- Multi-factor authentication (2FA). Authentication can be done through a user’s email, phone number, encryption key, or authenticator app. Typically, the last two options are the most secure ones, as they’re nearly immune to phishing attempts.
- Customizable access controls. Administrators should be able to dictate what users (internal employees as well as other third parties) can see, interact with, or download. If a data room has granular access controls, that’s usually a good sign (see below). These controls help you share your files on a need-to-know basis — a security best practice that will go a long way towards preventing information leakage.
- Data backup and recovery. A good data room should make it easy for users to regularly backup their data — and to recover their backup points without any hassle, should any documents be lost or damaged. Backups are particularly important to prevent ransomware attacks — something that 65% of financial organizations worldwide were faced with in 2024.
If a data room includes all these security features, it will likely be more than well equipped to ensure your sensitive data remains protected from unauthorized access, both during file sharing and storage. Look for providers that emphasize robust audit trails and activity monitoring for enhanced transparency and accountability.
2. Check compliance and certifications
Ensure the VDR complies with industry standards. Look for:
- ISO 27081. This ensures data protection and privacy in cloud storage environments and is a key framework for managing sensitive information securely.
- SOC 2. The focus here is on the management of data based on five trust service criteria: security, availability, processing integrity, confidentiality, and privacy.
- FINRA. FINRA regulates the securities industry and requires firms to protect sensitive customer data and maintain strict record-keeping practices.
- GDPR. The General Data Protection Regulation mandates explicit consent for data processing, and includes the right to access and the right to be forgotten for individuals in the European Union.
- HIPAA. Protects electronic protected health information (ePHI) through stringent security measures, ensuring patient privacy in the healthcare sector.
These and similar certifications indicate VDR compliance, meaning the data room in question follows stringent security practices and meets the necessary regulatory requirements. This is especially critical in heavily-regulated industries like finance, legal, and healthcare.
3. Consider ease of use
While security is vital, your data room should also be user-friendly enough to facilitate the onboarding of new users — including the less tech-savvy.
With that in mind, look for a platform that balances strong security measures with intuitive navigation and simple file management. A data room with a steep learning curve may hinder productivity far down the line, so opt for one that your team can adopt easily, without sacrificing data protection and privacy.
Intuitive, easy-to-use data rooms will often include the following features, among others:
- On-platform messaging and communication
- Automatic file indexing and numbering
- Mobile user interface
- Easy drag-and-drop upload
- Single Sign On (SSO) login
- Multilingual access
- Compatibility with multiple devices (including Android and iOS apps)
For a more streamlined experience, you may also want to look for data rooms that don’t require you to install extra plugins or work through specially-designed APIs.
4. Compare providers and features
Not all data rooms offer the same features — or pricing!
Compare your shortlist of providers based on the specific needs of your business — things such as scalability in number of users and storage capacity, speed of customer support, and integrations with other software and plugins that your team may need for its daily workflows. Check out reviews or even go ahead and request demos to get a better idea of your provider finalists.
Finally, if you’re fairly set on your final choice, consider starting with a free trial period (when available) to test how well the data room performs for your specific use cases.
Additional security features to consider
Beyond basic security measures, several advanced features can further protect your sensitive data in a Virtual Data Room (VDR). These will add extra layers of control and visibility, bringing you a greater degree of peace of mind and providing an extra guarantee that critical documents will remain secure throughout their lifecycle.
Watermarking and document permissions
Watermarking is an effective way to deter unauthorized distribution of sensitive documents. VDRs with customizable watermarking options allow you to watermark documents, automatically embedding identifying information (like usernames or timestamps) directly into files and making it clear who accessed or downloaded them. This discourages unauthorized sharing and helps prevent document leaks.
As for document permissions, granular control will go a long way towards preventing undesired user actions. With granular settings, administrators can restrict downloads or prevent users from editing, or printing documents, thus ensuring that files are only accessed according to specified roles and viewed solely on a need-to-know basis.
Needless to say, this tight control over who has eyes on your files will reduce the risk of accidental as well as intentional misuse of sensitive information.
IP monitoring and user alerts
IP monitoring in virtual data rooms enhances data room security by tracking the locations from which users access the system. When you monitor IP addresses, you are able to identify unusual login locations or patterns that could indicate unauthorized access. On the other side of that feature, suspicious activity alerts will notify administrators in real-time, allowing them to take immediate action should any red flags come up.
It’s useful to note that user alerts can be customized to track specific actions — anything from multiple failed login attempts to access outside of normal business hours for a given timezone. These proactive measures help prevent security breaches and ensure an automatic, continuous monitoring of all activity in the virtual data room.
Fence view and remote shred
If you take security seriously, take it up an extra notch with other features such as fence view and remote shred.
Fence view: Allows you to share files in a restricted viewing mode especially designed to prevent camera attacks. Users are only able to see parts of the file in question, while the rest is kept blurred or blocked out of sight until the user scrolls down to it.
Remote shred: When remote shred is enabled in your data room, you will be able to delete files even after they’ve been downloaded to other users’ devices. This is a powerful feature that helps you retain control over key documents even when they’re long out of your sight.
| Security Feature | Description |
| 256-bit encryption | Ensures sensitive data is encrypted both in transit and at rest, preventing unauthorized access. |
| Multi-factor authentication (MFA or 2FA) | Adds an extra layer of security by requiring a second verification method for login. |
| Access control | Allows administrators to assign specific permissions, restricting who can view, edit, or download documents. |
| Audit trails | Allow you to monitor user activity, providing a clear record of document access and changes for compliance and monitoring. |
| Watermarking | Embeds identifying information in documents, discouraging unauthorized distribution and enabling traceability. |
| IP monitoring | Tracks the geographic locations of user logins to identify unusual or suspicious access patterns. |
| User alerts | Sends notifications for specific actions, such as suspicious login attempts or unusual document activity. |
| Document permissions | Provides granular control over document access, restricting actions like downloading, printing, or editing. |
| Data backup and recovery | Ensures regular backups of stored data and allows for quick recovery in case of data loss. |
| Fence view | Inhibits camera-based attacks by restricting the field of vision a user has over given files. |
| Remote shred | Gives admins control to remotely destroy files that have been downloaded from the data room. |
Data room use cases by industry
With virtual data room adoption at its highest rate in history, — and indeed projected to reach $13.22 billion by 2032 — it’s worth taking a look at some use cases that show us how businesses are adapting to the new tech.
Financial services
JPMorgan Chase, one of the world’s largest financial institutions, uses virtual data rooms to facilitate complex transactions such as M&A, capital raising, and due diligence processes — all of which are high-stakes environments with vast amounts of sensitive financial documents being exchanged between multiple parties.
By using a secure data room, JPMorgan ensures that confidential information is protected through encryption, 2FA, and strict access controls. Only authorized individuals are allowed to view or edit critical documents, which allows for a more efficient collaboration with strict security standards.
The finance industry giant also relies on data rooms to meet regulatory requirements — audit trails help track user activity and ensure compliance with industry standards like ISO and SOC 2.
Energy and renewables
Eletrobras, the largest power utility company in Latin America, uses Ideals virtual data rooms to manage its complex energy projects and transactions in the renewables sector. With Ideals, Eletrobras ensures that key confidential documents related to bids, project financing, and regulatory compliance are protected through encryption and access controls, allowing secure collaboration with partners and stakeholders.
The Ideals data room also helps Eletrobras maintain transparency and accountability, especially in large-scale energy projects that require regulatory oversight. Audit trails and activity monitoring features provide full visibility into document access, ensuring compliance with industry regulations while minimizing the risk of data breaches. This enables Eletrobras to efficiently manage transactions while safeguarding sensitive data in the highly regulated energy sector.
Pharma and life sciences
A well-known example of a key VDR collaboration: Pfizer and AstraZeneca leveraged a virtual data room to securely manage sensitive data during their collaboration on COVID-19 vaccine development. The data room allowed both companies to share critical information, including clinical trial data and manufacturing processes, while maintaining strict confidentiality. The secure platform allowed for real-time collaboration on a global scale, while safeguarding key data and speeding up decision-making in a high-stakes situation where time was of the essence.
The use of a VDR was essential in protecting intellectual property and regulatory information, all while providing audit trails to track document access and ensure compliance. Pfizer and AstraZeneca maintained data security and transparency — so crucial in the world of pharma —, thanks to their use of a data room.
Tech and telecom
Valsoft, a company specializing in acquiring and growing software businesses, uses data rooms to manage confidential information during its acquisitions in the tech and telecom sectors.
With VDRs, Valsoft can securely share documents of key importance, including financial records, intellectual property details, and business strategies, with stakeholders and potential partners, keeping critical data protected throughout the due diligence process.
Data rooms also allow Valsoft to streamline complex transactions, maintain transparency and compliance, and accelerate deal timelines — all while safeguarding sensitive information in the fast-moving tech and telecom industry.
To cap off
In today’s landscape, one thing is abundantly clear to businesses everywhere: securing sensitive information is key.
This is why a well-equipped virtual data room is a must. With a perfect balance of protection and functionality, a good data room will help you remain protected with features such as:
- Access controls
- Multi-factor authentication
- Audit trail
- Advanced tools such as watermarking and IP restrictions
These and other functionalities will give you a solution that not only keeps your data safe, but helps you streamline your business projects and collaborations. Choose the right data room and you will find yourself managing the most complex and high-stakes transactions with confidence and competence, knowing your data is protected every step of the way.
Time to choose your data room? Check out our home page for a detailed, feature-by-feature comparison of top virtual data rooms!